SUMMARY
This is AI generated summarization, which may have errors. For context, always refer to the full article.
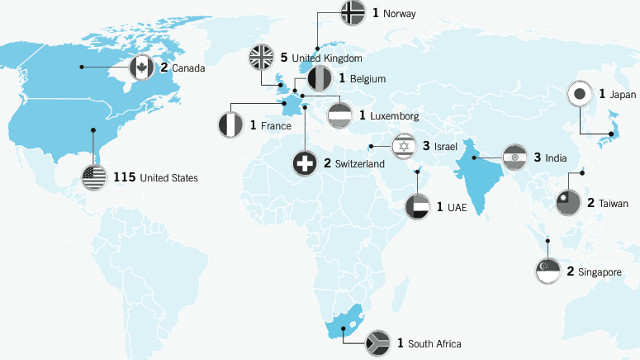
MANILA, Philippines – Mandiant, an American computer security firm, released a report and appendix outlining evidence that suggests a Chinese military unit is responsible for a sustained series of cyberattacks against various companies and institutions around the world.
The Mandiant report’s (full PDF here) executive summary said that details of an Advanced Persistent Threat (APT) analyzed through hundreds of investigations “convince us that the groups conducting these activities are based primarily in China and that the Chinese Government is aware of them.”
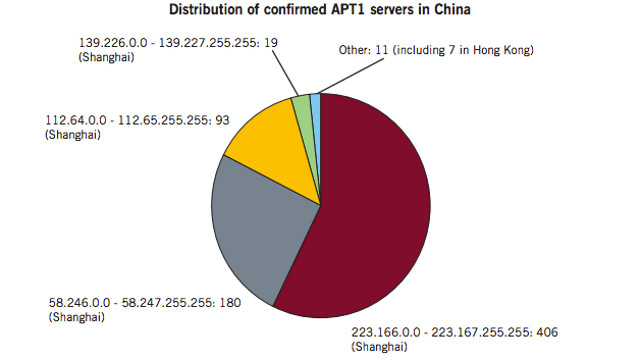
Some of the findings in the report explained that APT1, the most prolific group of the Advanced Persistent Threats, is located in Datong Road in Gaoqiaozhen, within Shanghai. The 2nd Bureau of the People’s Liberation Army (PLA) General Staff Department’s (GSD) 3rd Department, otherwise known as Unit 61398, is also located there.
Mandiant’s research also found PLA’s Unit 61398 “is similar to APT1 in its mission, capabilities, and resources.”
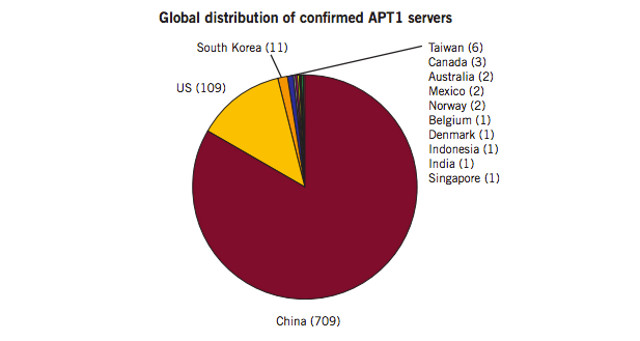
In its investigation of APT1, Mandiant raised two possibilities. The first is that Unit 61398 may be APT1.
The other possibility, the firm wrote, is that “A secret, resourced organization full of mainland Chinese speakers with direct access to Shanghai-based telecommunications infrastructure is engaged in a multi year, enterprise scale computer espionage campaign right outside of Unit 61398’s gates, performing tasks similar to Unit 61398’s known mission.”
This Advanced Persistent Threat report is separate from the hacking attempts made on news organizations like The New York Times and The Wall Street Journal, though one mention of this particular report by Mandiant is done in a news piece written by The New York Times (linked below).
The New York Times article on the Mandiant report noted the importance of the firm’s report on US interests and security.
As the New York Times report explained, the escalating nature of the attacks over time “focus not just on stealing information, but obtaining the ability to manipulate American critical infrastructure: the power grids and other utilities.”
Despite this, the American government is hesitant to link the two groups due to diplomatic issues.
US President Barack Obama has taken initial steps to protect the country, however, by alluding to this in his State of the Union address. As he said in his speech, “Now our enemies are also seeking the ability to sabotage our power grid, our financial institutions, and our air traffic control systems. We cannot look back years from now and wonder why we did nothing in the face of real threats to our security and our economy.”
He also signed a Cybersecurity Executive Order to increase information sharing for national security purposes. – Rappler.com
Add a comment
How does this make you feel?
There are no comments yet. Add your comment to start the conversation.