SUMMARY
This is AI generated summarization, which may have errors. For context, always refer to the full article.
MANILA, Philippines – As the world grows more connected online, the potential for security threats to come to the Internet grows more severe, and it’s less a matter of if an attack will happen, but when it will take place.
This is the reality presented by a series of reports done at PROTECT 2013, a conference held on April 17 at the Intercontinental Hotel Manila.
Amit Jain, the lead solution architect at Trustwave, a security information firm, talked about the realities facing global security today as a result of the Internet and the proliferation of mobile devices.
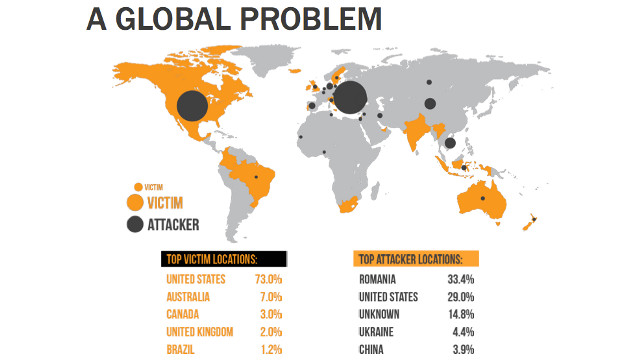
In his presentation, which takes its cue from the Trustwave 2013 Global Security Report, Jain presents evidence that suggests cyber attacks are a global problem, with the United States being the most hounded victim by attackers.
If this doesn’t seem like something of personal interest, it’s important to note that any data an individual has is worth something to the right person on the black market, which is why cyber security is important.
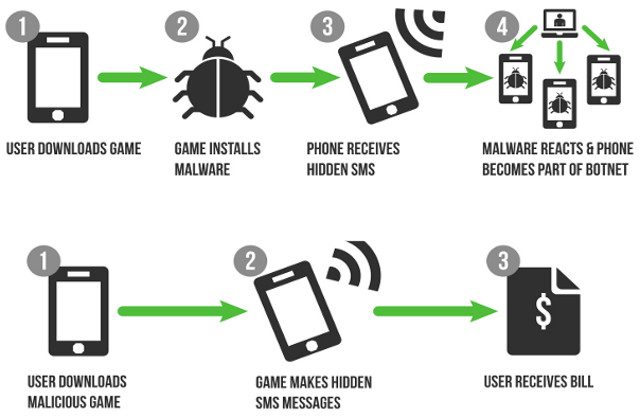
Through Trustwave’s analysis, the company noted that cybercriminals are continuing their offensive, with e-commerce applications being the top targeted asset. Mobile malware has also grown 400% from 2012 (70,000 to 280,000 instances of mobile malware) to become a swiftly rising threat to the security of home and office networks.
The report also noted that websites and email are the most common ways to attack users. Worse still, general self-detection of a security breach is still rather slow. With businesses, for example, the time from intrusion to containment can take an average of 210 days.

Towards robust mechanisms
Tim Scyner, Regional Security Director (APAC) of Sykes Asia, Inc., took another approach to discussing security in his presentation. Instead of focusing on global security issues, Scyner processed the same concerns of Amit Jain from his personal viewpoint as the one who has to deal with securing data in the workplace.
Scyner noted that a typical workplace has data everywhere that is in need of securing, from the computers being used, to the devices in one’s pocket. He makes special mention of the sticky notes and papers that contain sensitive information but is otherwise left for people to discover and take at their leisure.
The basic idea to maintain security is to create a robust protection mechanism by having an effective mix of policies or workplace rules, processes or methods of action, technology or infrastructure to handle security and reduce issues in a worst-case scenario, and people who understand what’s at stake and can observe the policies and processes.
By doing this, companies and individuals can prevent unauthorized people from accessing sensitive data, detect a breach or potential situation in the making, and respond to an event and mitigate damage.
Bitter medicine
Going back to Jain’s talk, it would be safe to say he expounds on the creation of robust mechanisms by offering solutions to remedy common issues with various sectors in the technology sphere.
For those making applications, Jain advises proper training of developers. Not only should developers of all sorts be reviewing code and testing the systems for issues, it should also be ready to protect what they’ve developed in real time and allow for any new issues to be patched quickly.
For those using mobile devices in the workplace, Jain and Scyner agree that there should be mobile device access policies in place to prevent issues from occuring to begin with.
Companies should think about improving access control technologies, as well as using strong authentication for users and devices, such as two-factor authentication. Security information and event management (SIEM) solutions should also be in place to track down and analyze security alerts made by network hardware and applications.
Those using web, social networks, and email should also have a plan since unauthorized access through such methods need to be noted as well. Aside from readying resilient anti-malware systems to protect networks, patching and scanning for vulnerabilities should be done regularly by individuals and companies.
Lastly, end-users and company employees have an important part to play. All should be aware of both the role proper security plays in a network and the policies that need to be implemented to maintain good security.
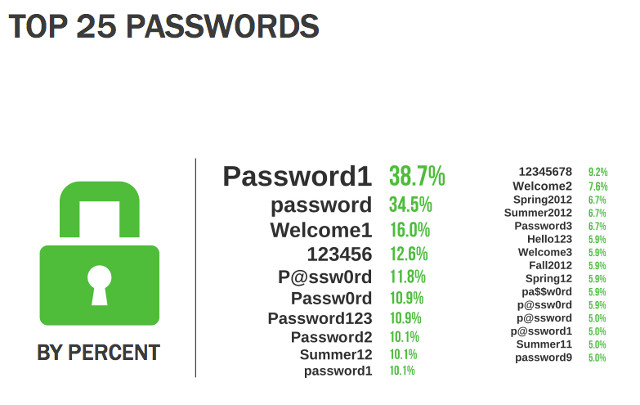
Strong authentication should be taken advantage of, and people should consider using longer passphrases instead of passwords to secure their information. If possible, people should also set up their own attack simulations and drills in the event of a security crisis.
The bitter medicine is hard to swallow, but important to take seriously: the loss or theft of data is a calamity all its own, and these possibilities shouldn’t be underestimated by anyone who’s connected online. – Rappler.com
Add a comment
How does this make you feel?
There are no comments yet. Add your comment to start the conversation.