SUMMARY
This is AI generated summarization, which may have errors. For context, always refer to the full article.

MANILA, Philippines – If you wanted to bring a country into the 21st century, but wanted to keep everything everyone did under your watchful eye, what would you do?
If you’re North Korea, the answer would be to build your own operating system (OS) – RedStar OS – where the state’s control over the information going in and out of the computer is absolute.
A presentation at the Chaos Communication Congress in Hamburg, Germany, on Sunday, December 27, investigated how RedStar OS’ third version went against the principles of open source development, despite being made from freely available software meant for free speech purposes.
Niklaus Schiess and Florian Grunow, the pair who presented the investigation into RedStar, described to Motherboard that the OS looked like Mac OSX, but was based on Fedora 11 – a 2009 Linux distribution – and worked with an operating system kernel from 2011.
It included word processing and music creation software and a modified version of the Firefox browser.
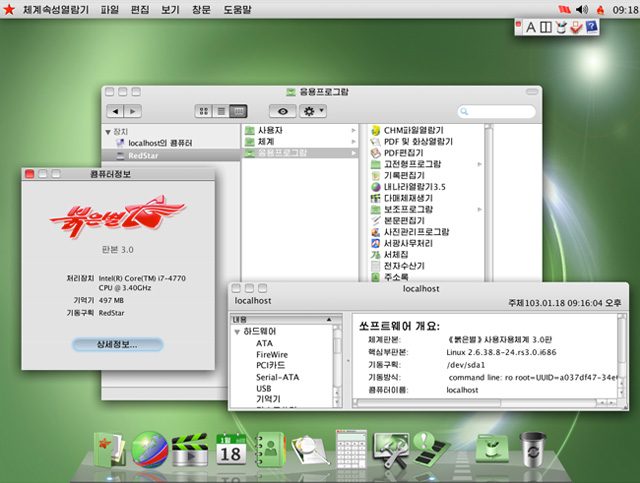
Aside from these features, everything else seemed to make it poised to track down users’ actions. RedStar included a system in the OS that allowed it to monitor any changes a user might make, reacting according to the actions a user takes.
This extra system in place lets RedStar tag USB sticks with data watermarks, so it can track who has a particular file, who made it, as well as who opened it. Motherboard went on to say, “In short, whenever a USB storage device containing documents, photos or videos is inserted into a RedStar computer, the operating system takes the current hard-disk’s serial number, encrypts that number, and then writes that encrypted serial into the file, marking it.”
RedStar, according to Schless, is also “highly customized,” with a lot of features added “to improve the security of the system,” such as a pre-installed firewall, extra protections on some core system files, and a program that keeps checking the computer if changes are made to core files.
If the program sees a core file has been altered, it reboots the system immediately. This action, according to the researchers, can sometimes force an infinite cycle of reboots, depending on the circumstances.
The researchers also said the changes are apparently designed to protect the OS from its own users. Most notably, the OS functions were meant to be used only within North Korea, with its anti-virus system getting updates from a North Korean server and its browser pointing only to internal North Korean IP addresses.
Stranger still, even the encryption algorithms of the system have been tweaked so as not to rely on foreign cryptography. – Rappler.com
Add a comment
How does this make you feel?
There are no comments yet. Add your comment to start the conversation.