SUMMARY
This is AI generated summarization, which may have errors. For context, always refer to the full article.

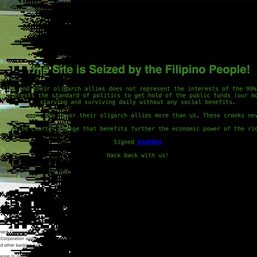
MANILA, Philippines – As the Philippine National Police (PNP) continues to probe its systems for the breach reported by cybersecurity firm VPNMentor on Tuesday, April 18, the question remains: Was the database accessed by another entity aside from VPNMentor?
It’s already established that there is indeed a breach. The PNP database should have been password-protected because it contained sensitive documents that could be used for identity theft, among other crimes. Yet, it wasn’t, enabling VPNMentor to get inside the database.
But VPNMentor and its team are ethical cybersecurity researchers whose function is to look specifically for such leaks in order to report them to the proper authorities.
The question is, during the minimum six weeks that the database was exposed, had any other non-authorized entity, perhaps one with less noble intentions, been able to access it?
Some online research points to a grim truth: Six weeks is more than enough time for a threat actor or a hacker to spot an exposed database, and exploit it.
First attack can occur just after 8 and a half hours
Comparitech, a tech comparison site comprised of cybersecurity researchers with a focus on VPNs (virtual private networks), password managers, and antivirus tools, among others, conducted a test to find the answer to the question, “If you leave a database unsecured on the web, how long does it take hackers to find and steal it?”
The team set up honeypots, which are essentially bait for hackers. They set up fake databases online with fake user data.
The data was left exposed for 12 days from May 11, 2020, to May 22, 2020. During that time, 175 unauthorized requests were made, which they broadly refer to as “attacks,” with an average of 18 attacks per day.
The first attack came on May 12, just 8 hours and 35 minutes after the team deployed the honeypots.
That means, in that amount of time an unauthorized entity was able to scan for the database, find it to be unprotected, and attempt to make requests to the server. Those requests could range from stealing, scraping or destroying the data, or changing the configuration of the server for their own gain.
According to Comparitech, many attackers use what is called an internet-of-things (IoT) search engine to locate vulnerable databases. In the case of Comparitech’s honeypot, more than three dozen attacks took place before an IoT search engine was able to scan it and include it in its index.
VPNMentor’s Jeremiah Fowler also noted the use of an IoT search engine to locate the reported exposed database.
“Some of the attackers could have plausibly been security researchers similar to our own team, but we often can’t distinguish between a malicious attacker and a benign one,” Comparitech said.
On May 29, 2020 – 19 days after the honeypot was deployed – a malicious ransomware bot discovered it, deleted the contents of the database, and requested payment.
In his assessment of the PNP breach, Fowler wrote he did not see evidence of cyber attacks or database encryption via ransomware.
Sophos finds even faster attacks
In an email interview with Rappler, Aaron Bugal, field chief technology officer of cybersecurity firm Sophos, emphasized the need for encryption for databases.
“In regards to the timing around finding and abusing exposed databases – they shouldn’t be exposed in the first place. At the very least, the data itself should be encrypted in place, and only when it needs to be presented through an application for official use should the data become human readable,” Bugal wrote.
Bugal discussed their own honeypot-type research in 2019, with entities finding their exposed systems in just 84 seconds.
“It can take seconds to minutes for a service on the internet to be published and then scanned/abused by automated systems put in place by cyber criminals.
In 2019, Sophos exposed a series of remote desktop protocol (RDP)-enabled desktop systems on the open internet as a form of advanced honeypot. It took a mere 84 seconds for the first brute force attack to start on one of these exposed systems.
Bugal offered advice to those who may have been affected in the Philippine police data breach.
“The systems breached that were hosting the exposed data associated with the Philippine nationals need to be forensically analyzed to understand if it has been accessed and transferred out of these systems. If it has, those affected need to be notified as soon as possible so they can closely monitor their physical and digital identities to ensure no fraudulent actions are undertaken against them,” Bugal said.
The National Privacy Commission (NPC) said they would be conducting their own on-site inspection of the Philippine police’s computer systems on Monday afternoon, April 24.
Michael Santos, the commission’s chief of complaints and investigation, told ANC on Friday, April 21, that the investigation would include matching the data provided by VPNMentor with the police’s data processing systems to see if indeed it was the police’s systems and database that were exposed.
They will look at computer logs to see who else had accessed the data and if there had been extraction of data. Santos said then that what they knew at the time was indeed a database “was left exposed.”
The NPC is expected to issue a statement after the investigation is processed and reported to NPC heads. NPC’s meeting with VPNMentor researcher Jeremiah Fowler pushed through on Friday, but the commission hasn’t yet released information on what was discussed.
Malware deployment, credentials theft
Similar honeypots were set up by US cybersecurity firm Imperva in their own study in 2020.
Six fake intentionally open databases were set up. The fastest it took for one database to be found and attacked was 10 hours. Others took 11, 15, and 16 hours while two others took longer at 240 hours (10 days) and 288 hours (12 days).
The two most common forms of attacks after a hacker was able to successfully connect to the database were the deployment of malware, and credentials theft.
“When it comes to databases, one of the most important rules is never to expose your database to public access. In cloud environments, however, it’s very easy to make this mistake because your cloud provider can allow it to happen with just a few clicks,” Imperva wrote.
While none of these studies are peer-reviewed, it provides some information as to how fast hackers can spot and exploit a vulnerability.
Without a definitive statement yet from the PNP, it’s best for possible victims to be on a close lookout for potential cases of identity theft, phishing, and other malicious activities. – Rappler.com
Add a comment
How does this make you feel?
![[OPINION] A big defeat for Big Tech](https://www.rappler.com/tachyon/2024/03/big-defeat-big-tech-march-27-2024.jpg?resize=257%2C257&crop=425px%2C0px%2C1080px%2C1080px)







There are no comments yet. Add your comment to start the conversation.