SUMMARY
This is AI generated summarization, which may have errors. For context, always refer to the full article.

MANILA, Philippines – Growing, cheap access to online connectivity – from low-cost smartphones to preinstalled applications – is giving rise to concerns about user privacy, specifically how cheap smartphones are siphoning user data and allowing backdoor access to sensitive information.
A case study from Privacy International released on Friday, September 20, described potential problem areas with preinstalled applications users should be aware of when it comes to purchasing phones, as well as reminding companies of their responsibility to all consumers, regardless of the amount of money they can invest into a phone or other device.
Studying MyPhone’s MyA2
In Privacy International’s case study, they recounted how a colleague who visited the Philippines needed to buy a cheap replacement phone and picked up MyPhone’s MyA2 for around $17. Upon the colleague’s return to the United Kingdom, they took a look at the phone and its preinstalled apps for privacy and security lapses.
The first thing the case study took into account was how old the mobile operating system was on the phone. It was running on Android 6.0.
MyPhone is touted as a “certified Android Partner,” so it should not be running outdated software, as old mobile OS versions may have vulnerabilities long since patched in more recent iterations of Android.
Privacy International also pointed out the phone was released in December 2017 with Android 6.x when Android 8.x was already out as of August, with the phone meeting minimum harware requirements for it – though it may not be certified as Android 8 ready. “It’s unclear because not all of those critera are public knowledge or clearly defined,” the study said.
For context, the report also mentions that aside from the particular MyA2 phone, earlier in the year there has been “a large-scale study of pre-installed software on Android devices – from more than 200 vendors” that also “found harmful behaviours and backdoored access to sensitive data and services without user consent or awareness.”
The MyPhone case study said the following preinstalled applications came with the device, aside from mainstays like Google’s services and basic functions like a clock and calculator:
- MyPhoneRegistration – An app for registering the device with the manufacturer
- Pinoy – A Portal app, providing various services, such as news, podcasts and well-being
- Facebook Lite – A slimmed version of the Facebook App
- Brown Portal – A portal with a browser-like interface for MyPhone users
The phone also had preloaded apps inside the file system, but were uninstalled:
- Baidu_Location – Location Service for Baidu Maps
- Xender – A tool for file synchronization and transmission
These apps, Baidu_Location and Xender, were likely meant for activation in MyPhone’s alternative market, China, rather than the Philippine market.
Privacy International thus used its app testing environment to look into the 4 preinstalled applications and found some more troubling insights.
MyPhoneRegistration and Brown Portal
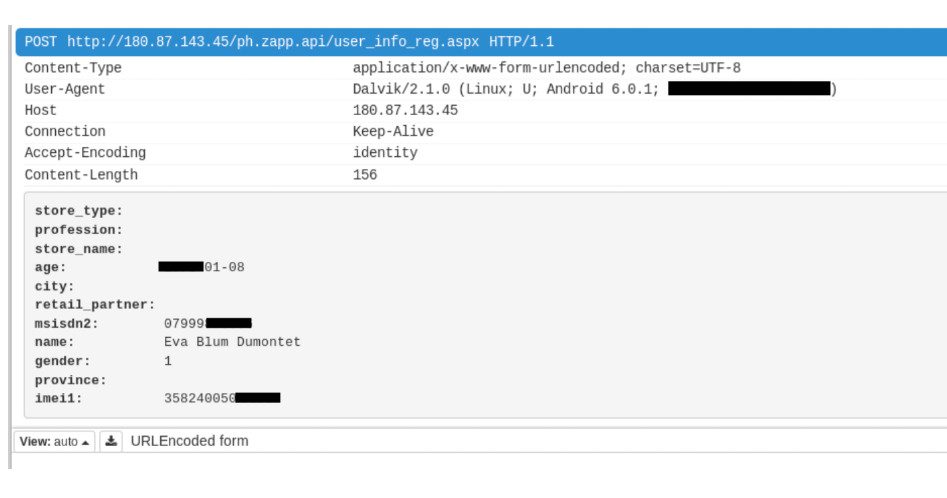
MyPhoneRegistration, an app that allows MyPhone users to register their phones with the company for ease of access to warranty information and software updates among other functions, was found to have attempted contacting a remote server without any security protocol.
Their report explained, “This means that personal information like your IMEI number (a unique number that identifies the device), name, date of birth, and gender are shared without encryption with Zed (the company hosting MyPhoneRegistration’s server).”
It added the server “is no longer at the path hardcoded into the app.’ This means the phone will just keep trying – but failing – to transmit details to the missing server.
But even if the server doesn’t exist anymore, the user is still vulnerable when connected, as the data will still be visible on networks that a person connects to, according to the report. “It does so insecurely, giving away the user’s name, gender, data of birth and IMEI to any network that the user connects to, for example Wi-Fi,” it said.
Because the app cannot be updated or deleted by users, it is also said to be permanently vulnerable to attack. Those with physical access to the phone can potentially run their own code and acquire the same high-level privileges as the MyPhoneRegistration app.
The preinstalled Brown Portal app, meanwhile, “can’t be deleted, also gets access to your network information and has location permission, which means your location can be tracked at all times.”
Pinoy app and Facebook Lite
Pinoy app appears to be more innocuous, allowing users to access paid and free services for religious or political purposes. These include jokes, bible quotes, Philippine cultural information and spiritual advice, among others.
But the case study points out Pinoy can also be problematic as it can, with user permission, “access the phone’s contacts, location, SMS, storage and make phone calls. The app cannot be deleted, and also communicates with Zed servers over an insecure channel.” This app cannot be updated as well, seeing as it’s not on Google Play.
Meanwhile, Facebook Lite, the data-friendly version of the Facebook app, can be updated using the Google Play store and uninstalled but not completely removed as it reverts to the preinstalled version when uninstalled. It asks for permission to access a user’s calendar, camera, contacts, location, microphone, phone, SMS and storage.
In March, Facebook was under fire for storing Facebook users’ passwords in plain text, with users of Facebook Lite affected too. The issue went as far back as 2012, with the passwords of anywhere from 200 million to 600 million people visible.
MyPhone responds
Privacy International contacted both Zed and MyPhone while making the report, though Zed did not reply before publication.
In an emailed statement to Privacy International on Tuesday, September 17, MyPhone responded:
“With our goal to deliver a unique experience to our end-users, we have pre-installed our in-house apps like Brown Portal, Pinoy and Registration, which bring contents based on their interest, promoting Pinoy culture, send them our latest product updates and services. In this way, we can continue to improve our future products and services we offer.
“At the same time, as we value the privacy of our user base, we have now our Privacy Policy accessible in our latest and upcoming devices that covers the collection, use, disclosure, transfer, and storage of their personal information.”
“We hope that you will reconsider the messaging that you want to convey on your article. We at MyPhone value the privacy of our consumers as well as you are and we are dedicated to improve our privacy controls towards acceptable standards.”
Call to action
Because of uneven protections for people across the world regarding their data, personal data privacy “becomes the price the economically disadvantaged have to pay to access a phone and the internet – from poor security to advertising through pre-installed apps,” the study stated.
“Since the phone is shipped with an out-dated version of Android, it comes with known vulnerabilities that will not be patched and that can be exploited cheaply by anyone, from scammers to government agencies,” it said.
Privacy International reiterated that companies should protect the consumers they serve, and being economically disadvantaged should not erode a person’s rights.
“Ultimately, pre-installed apps undermine Google’s product, especially from certified partners. It’s up to Google to make sure manufacturers using their trademarks don’t sully their brand, and don’t take advantage of economically disadvantaged people,” it concluded.
The full report is available here, while a detailed analysis and methodology is available here. – Rappler.com
Add a comment
How does this make you feel?
There are no comments yet. Add your comment to start the conversation.