SUMMARY
This is AI generated summarization, which may have errors. For context, always refer to the full article.

MANILA, Philippines – Computer company Lenovo installed adware into its new consumer computers, with the pre-installed adware becoming active after being turned on, according to a recently publicized Lenovo forum post.
The Next Web reported Thursday, February 19, that the Superfish adware was reportedly installed on Lenovo consumer laptops out of the box.
The Superfish adware, called VirtualDiscovery, injects third-party advertisements in Google searches and websites without requiring permission from the computer user – apparently affecting Internet Explorer, Mozilla Firefox, and Google Chrome on the Lenovo computers.
Mark Hopkins, a Lenovo community administrator, mentioned in late January that Superfish would be temporarily removed following complaints of unwanted behavior on computers.
Hopkins wrote: “Due to some issues (browser pop up behavior for example), with the Superfish Visual Discovery browser add-on, we have temporarily removed Superfish from our consumer systems until such time as Superfish is able to provide a software build that addresses these issues. As for units already in market, we have requested that Superfish auto-update a fix that addresses these issues.”
Hopkins added in his post that Superfish “comes with Lenovo consumer products only,” adding that it is meant to be “a technology that helps users find and discover products visually” by analyzing an image, looking for identical images in real time in a list of 70,000 stores for similar items, comparing the prices “so the user can make the best decision on product and price.”
Other users on Lenovo’s forums reported additional issues with Superfish, noting that the adware installs its own self-signed certificate authority, allowing it to look legitimate to browsers. This would allow the Superfish software to potentially monitor or otherwise snoop on secure connections.
A user showed an example of Superfish being active during access to a banking facility.
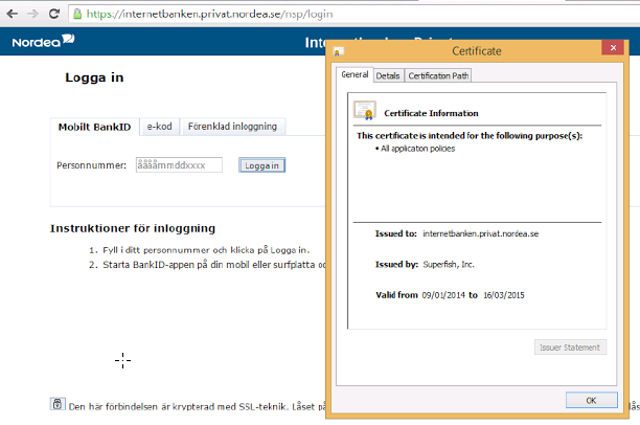
As The Next Web wrote, “This is a malicious technique commonly known as a man-in-the middle attack, where the certificate allows the software to decrypt secure requests, yet Lenovo appears to be shipping this software with some of its products out of the box.”
Users can attempt to uninstall Superfish by checking out this video for further assistance. – Rappler.com
Add a comment
How does this make you feel?
There are no comments yet. Add your comment to start the conversation.