SUMMARY
This is AI generated summarization, which may have errors. For context, always refer to the full article.

MANILA, Philippines – A vulnerability on the Makati COVID-19 relief portal, Proud Makatizen, was discovered and reported by VPN (virtual private network) review site and cybersecurity research firm, VPNMentor.
While VPNMentor reviews VPNs, the firm also has a cybersecurity research team called The Research Lab, whose works in the past include uncovering a 2019 data breach in Ecuador involving 20 million individuals as reported by The New York Times; a 2019 breach on US government and military personnel and a 2020 breach of a live webcam porn network as reported by the BBC; and a breach of a Chinese online shopping site that exposed millions of individuals as reported by TechCrunch.
What was the vulnerability?
VPNMentor explained that the Proud Makatizen website was using an “S3 bucket” from cloud computing services provider Amazon Web Services (AWS). AWS’ S3 is a popular enterprise cloud storage solution, which uses “buckets,” which are similar to a Google Drive folder. It’s a service that a website owner might procure from a provider to give their website an ability to store files from users.
But VPNMentor warned, in its report provided to Rappler, that “it is up to the users [of the S3 bucket] to properly define the security settings to protect any data stored therein.” It said that Proud Makatizen “failed to implement security measures on its S3 bucket, leaving the contents totally exposed and easily accessible to anyone with a web browser, and technical skills.”
How are S3 buckets secured?
VPNMentor explained that “open, publicly viewable S3 buckets are not a flaw of AWS” and are usually the result of “an error by the owner of the bucket.” Buckets can be made private, and can be given authentication protocols and multiple layers of access protocols. It is also important to follow best practices on authentication from the service provider, which in this case is AWS, added VPNMentor.
In Proud Makatizen’s case, “the Makati government did not properly configure the AWS S3 bucket in order to secure this personal information.”
Timeline from date of vulnerability discovery to the vulnerability being secured
VPNMentor reported as well the date when it discovered the vulnerability, when it made the report to CERT-PH (Computer Emergency Response Team – Philippines) – a division under the Cybersecurity Bureau of the Department of Information and Communications Technology – and when the Makati government secured the vulnerability:
- Date discovered by VPNMentor: March 30, 2022
- Date CERT-PH contacted: March 31, 2022
- Date of CERT-PH response: March 31, 2022
- Date CERT-PH report sent to City of Makati: April 4, 2022
- Date bucket was found secured: April 7, 2022
“We quickly identified Proud Makatizen as the owner of the data largely because the names of folders in the [S3] bucket matched the names of services offered on the Proud Makatizen website,” explained VPNMentor.
After confirming Proud Makatizen as the owner of the data, VPNMentor notified and coordinated with CERT-PH.
“They replied quickly and asked us to provide more information. We disclosed the URL leading to the unsecured server and provided further detail about what it contained. We received regular communication with Philippines CERT until they were able to complete their report and send it to the City of Makati. The AWS S3 bucket was secured shortly after,” explained VPNMentor.
CERT-PH confirmed the reported vulnerability to Rappler on Friday, July 1 via email. “We can confirm that the incident was reported to us by VPNMentor last March 31, 2022. We have notified the City of Makati (Makatizen) regarding the alleged issue. On April 7th, the Makati City Government’s ICT Office replied to us with their actions taken and remediation. The ticket was closed afterward,” a spokesperson from CERT-PH’s incident response division said.
How many could potentially be affected by the vulnerability, and what are its harmful effects?
VPNMentor estimated that about 300,000 individuals were potentially exposed from May 2020 to April 2022. About 620,000 files including passport, medical information, bank transactions, and proofs of payment were potentially exposed, with the total size of all the files at 39.7 gigabytes.
The Proud Makatizen website is a portal to Makati services for COVID-19 vaccine registration, COVID-19 financial aid, and tax payments, among others.
Regarding the amount of individuals potentially affected, VPNMentor explained, “The amount of individuals affected is an assumption according to the sample we analyzed for our responsible disclosure. As you can see, it’s a round number because we can only assume as our ethics require us to analyze a smaller sample, and not the whole database.”
What files and types of information were potentially exposed?
Identity documents
To register for vaccination or get aid, users needed to upload ID documents such as passports, driver’s licenses, and senior citizen cards. There were about 300,000 of these identity documents in the bucket, exposing names, photographs, addresses, ID numbers, and ID expiration dates, which could be used in identity theft and fraud.
Examples:


Medical documents
There were about 200,000 files and images of physician letters and prescriptions that proved a user had comorbidity or a pre-existing condition, as part of the process of getting a vaccine. The name, address, age, and the medical conditions can be seen in these medical prescriptions. Example:

Financial documents from companies
Makati businesses registered to take part in the Makati Assistance and Support to Businesses (MASB) program. VPNMentor found “several files” that may pertain to the finances of a certain company, making them eligible for the assistance program. These documents showed “transaction dates, account numbers, and names of accounts.”
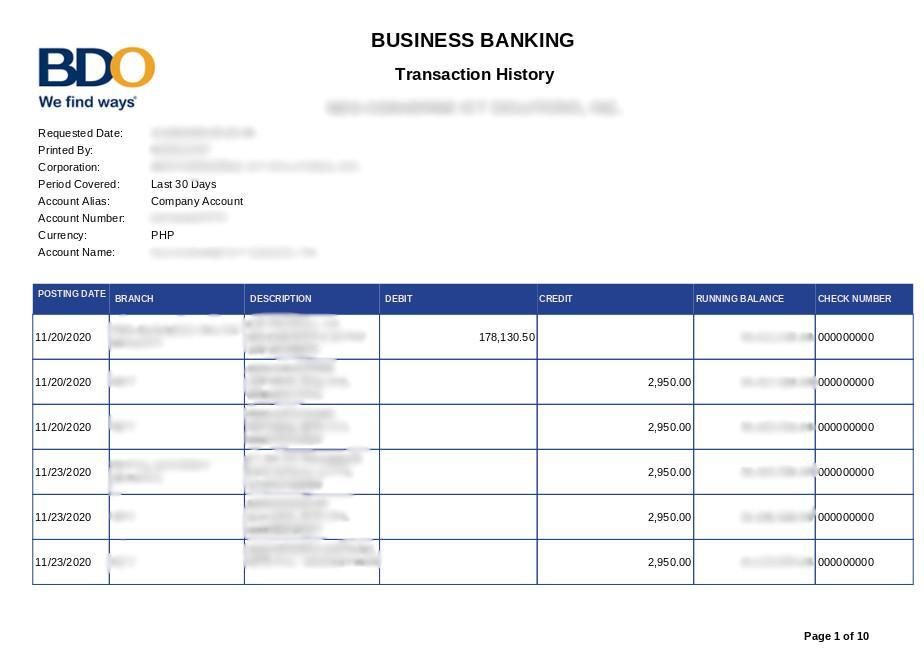
GCash payment confirmation messages
There were 12,000 of this type of files, showing the confirmatory message that a GCash sender receives when completing a transaction.
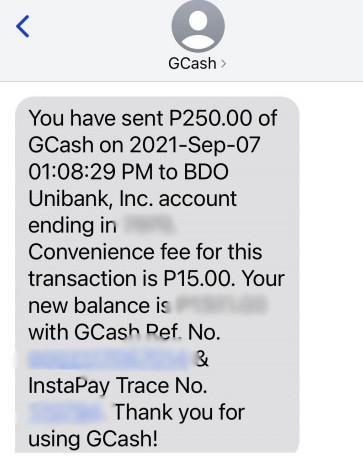
All in all, these types of documents being potentially exposed opened up an estimated 300,000 individuals to identity theft, tax fraud, insurance fraud, mail fraud, and phishing. However, while VPNMentor reported the vulnerability, the firm doesn’t have information whether criminal hackers or hacker groups found and exploited the vulnerability themselves before it was secured.
It is also unclear for how long the vulnerability was open. It would be the website owner, in this case the Makati government, that would have logs as to whether the open S3 bucket was accessed by other unauthorized individuals.
While the S3 bucket started storing data in May 2020, according to VPNMentor, there is also the possibility that the misconfiguration of the bucket could have happened later.
“From our experience, it doesn’t have to take long before different actors – it can be people like us who do this for ethical reasons, or it can be criminals, or it can even be nation-states – find these vulnerabilities,” said Noam Rotem, the cybersecurity specialist who led the VPNMentor research team.
The National Privacy Commission (NPC) told Rappler that they did not receive a report from the City of Makati, saying that “a system vulnerability does not automatically mean there is a personal data breach.” Alarmingly, both VPNMentor and the NPC both noted that this type of incident where there is a failure to restrict an S3 bucket is a common vulnerability not only in the Philippines but globally.
“This type of incident is, unfortunately, quite common and that’s one of the reasons why we are sharing our findings, in order to raise awareness and to help lower the risks of this happening.
“Unfortunately, the users have very little control over this. The only thing we always advise people to do is to put pressure on these organizations, whether commercial or government, to be responsible, and to have consequences for these kinds of exposures,” Rotem said.
Rappler reached out to the City of Makati prior to the article’s publication. They released a statement after the article’s publication. The city’s spokesperson Michael Camiña said: “There was no data breach with the data servers of the Makati City government. The subject system alleged to have been breached was a former development server containing fictitious test data. It is no longer online.” He added that no actual personal data has been compromised, and that the city government is committed to protecting personal information. – Rappler.com
Add a comment
How does this make you feel?

![[OPINION] We should own our health](https://www.rappler.com/tachyon/2024/06/thought-leaders-we-should-own-our-health.jpg?resize=257%2C257&crop=271px%2C0px%2C720px%2C720px)

![[OPINION] A big defeat for Big Tech](https://www.rappler.com/tachyon/2024/03/big-defeat-big-tech-march-27-2024.jpg?resize=257%2C257&crop=425px%2C0px%2C1080px%2C1080px)





There are no comments yet. Add your comment to start the conversation.